Perfecting self-driving technology is no small feat. From refining algorithms to navigating legal complexities, numerous obstacles remain. Despite these challenges, the prospect of autonomous vehicles promises a future of safer and more efficient travel.
Sustainability and Environmental Concerns
Environmental sustainability is now a top priority for automakers, who are designing vehicles with greater fuel efficiency and reduced carbon footprints. This push toward eco-friendly practices is a direct response to escalating environmental concerns and is shaped by both consumer preferences and regulatory requirements. The industry's future will undoubtedly hinge on sustainable innovation.
Transitioning to greener technologies is not without hurdles. The financial burden of adopting these solutions can be high, and ensuring accessibility for all consumers remains a challenge. However, the urgency of environmental conservation demands proactive measures, and the automotive sector is stepping up to the task.
The Impact of Connectivity and Information Technology
Modern vehicles are becoming increasingly connected, integrating features like infotainment systems, real-time navigation, and traffic updates. These innovations provide a more personalized and seamless driving experience.
Vehicle-to-everything (V2X) communication is another breakthrough, enabling cars to interact with infrastructure, other vehicles, and pedestrians. This interconnectedness is set to revolutionize transportation, enhancing both safety and efficiency. As technology continues to evolve, the line between cars and digital ecosystems will blur even further.
The Role of Government Regulations and Policies
Government policies are instrumental in steering the automotive industry toward innovation and safety. Regulations on emissions, fuel efficiency, and safety standards directly influence vehicle design and manufacturing. Incentives such as subsidies can also drive consumer adoption of new technologies, accelerating industry shifts. Effective policymaking is key to fostering sustainable progress.
Policymakers face the challenge of balancing innovation with risk management. As the sector evolves, ongoing adjustments to regulations will be necessary to address emerging complexities.
Future Trends and Innovations
The automotive industry is in a constant state of flux, with advancements in autonomy, electrification, and connectivity shaping its trajectory. The fusion of these technologies is paving the way for a more automated and interconnected driving future.
Personalization will also play a pivotal role, with vehicles increasingly designed to meet individual preferences. Driven by technological progress and consumer demand, this trend highlights the growing emphasis on customization in automotive design.
Identifying Potential Attack Vectors in Connected Car Systems
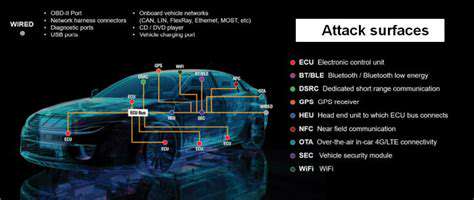
Understanding Attack Vectors
Attack vectors are the methods cybercriminals use to infiltrate systems or networks. Recognizing these pathways is essential for preemptively addressing vulnerabilities and strengthening defenses. Proactively identifying and neutralizing attack vectors is fundamental to a robust security framework. These threats can range from basic exploits to highly sophisticated attacks.
Knowledge of different attack vectors—such as malware, phishing, and network weaknesses—helps organizations develop targeted security measures. This enables the creation of effective policies that reduce the likelihood of breaches.
Network Vulnerabilities
Weaknesses in network security often arise from misconfigurations, outdated software, or inadequate firewalls. Exploiting these gaps, attackers can access confidential data or disrupt operations. Unsecured Wi-Fi networks, for instance, provide an easy entry point for eavesdropping, posing a serious risk in today's digital landscape.
Mitigating network vulnerabilities demands a proactive stance, including routine security checks, stringent access controls, and timely updates to patch known flaws.
Malware Infections
Malware, encompassing viruses, worms, and ransomware, poses a significant threat to system integrity. These malicious programs can steal data, cripple operations, or even hold systems hostage. Awareness of malware types and their potential impacts is critical for crafting effective countermeasures.
Deploying strong antivirus solutions, keeping systems updated, and educating users on malware risks are vital steps in maintaining security.
Social Engineering Tactics
Social engineering preys on human psychology to extract sensitive information or coerce actions that compromise security. Common tactics include phishing emails and fraudulent calls designed to deceive targets. These schemes are often highly convincing, making them a persistent threat. Regular training and strict security protocols are key to minimizing risks.
Phishing Attacks
Phishing remains a widespread threat, with attackers masquerading as trusted entities to steal credentials or financial details. These scams exploit trust to bypass security measures, making robust email filtering and multi-factor authentication essential defenses.
Physical Security Risks
Physical breaches—such as unauthorized access to sensitive areas or improper disposal of confidential materials—can undermine security. Weak access controls, insufficient surveillance, and lax document handling are common vulnerabilities. Implementing measures like access cards, CCTV, and secure disposal protocols helps mitigate these risks.
Supply Chain Vulnerabilities
Third-party vendors can introduce security gaps if not properly vetted. Attackers may exploit these weaknesses to infiltrate systems or implant malicious code. Rigorous vendor assessments, supply chain security protocols, and regular audits are crucial for minimizing exposure.