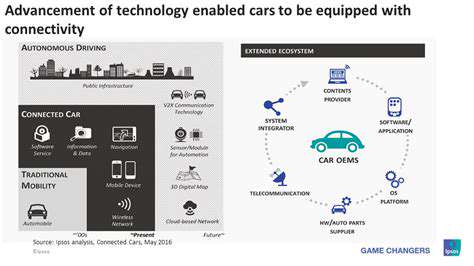
Defining Ethical Frameworks for Hacking Prevention
Defining Ethical Considerations in AI-Powered Healthcare
Artificial intelligence (AI) is rapidly transforming healthcare, offering unprecedented opportunities for diagnosis, treatment, and patient care. However, the integration of AI systems necessitates a careful examination of ethical implications. These considerations are crucial for ensuring that AI technologies are developed and deployed responsibly, promoting equitable access, and maintaining patient trust. AI algorithms need to be trained on diverse and representative datasets to avoid perpetuating biases that could lead to disparities in care for specific demographics.
One key ethical concern revolves around data privacy and security. AI systems often rely on vast amounts of patient data, raising concerns about the potential for breaches and misuse. Robust data protection measures and transparent data governance policies are essential to safeguard patient information and build public trust. Furthermore, ensuring that algorithms are explainable and understandable is vital for promoting accountability and trust in the AI-driven healthcare system.
Addressing Algorithmic Bias in AI Healthcare Applications
AI algorithms, when trained on biased data, can perpetuate and even amplify existing societal inequalities. This can lead to inaccurate diagnoses, inappropriate treatment recommendations, and unequal access to care for certain populations. Therefore, it is crucial to develop and implement methods to mitigate bias in AI systems, ensuring they are fair and equitable for all patients.
Careful consideration must be given to the data used to train AI models. Data sets should be thoroughly examined for potential biases, and steps should be taken to address any imbalances. This includes actively seeking diverse data sources and ensuring that the data reflects the full spectrum of the population it will serve. Furthermore, ongoing monitoring and evaluation of AI systems are essential to identify and correct any emerging biases.
Ensuring Transparency and Accountability in AI-Driven Healthcare
Transparency and accountability are paramount in the development and deployment of AI in healthcare. Understanding how AI systems arrive at their conclusions and recommendations is crucial for building trust and ensuring quality care. Clear and accessible explanations of AI algorithms are needed, allowing healthcare professionals to understand the reasoning behind diagnoses and treatment plans. Such transparency helps to identify potential errors and biases, enabling corrective actions and promoting confidence in the AI systems.
Establishing clear lines of accountability is equally important. Determining responsibility when errors occur or when unforeseen issues arise is necessary. Robust mechanisms for oversight and independent review of AI systems should be implemented to ensure their ethical and responsible use. This includes creating avenues for patients to raise concerns and for independent audits to assess the performance and ethical implications of AI systems.
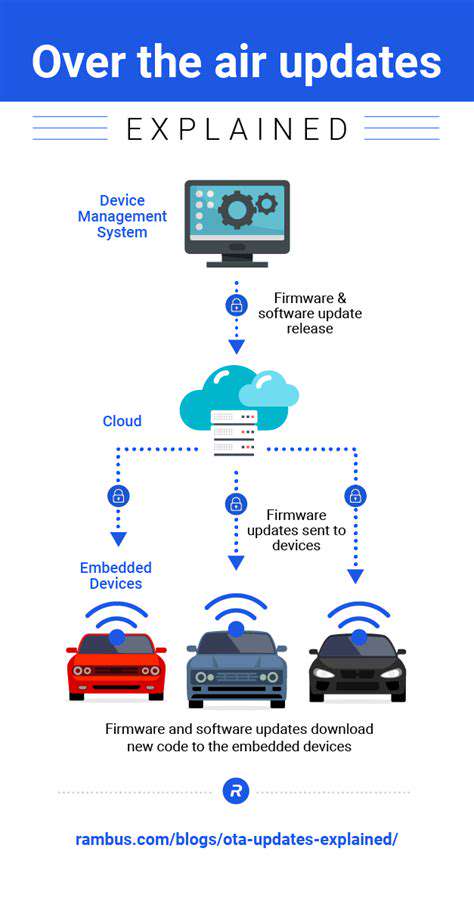
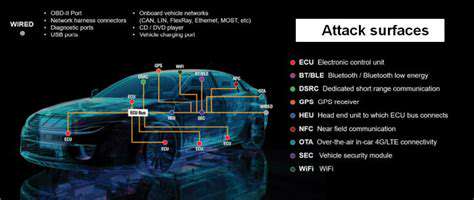
The Role of Data Privacy and Security in AV Hacking Prevention

Data Privacy Fundamentals
Data privacy is a cornerstone of responsible data handling, encompassing the principles of collecting, using, and storing personal information ethically and legally. It's about respecting individuals' rights to control their personal data and ensuring that this information is protected from unauthorized access, use, or disclosure. Understanding the legal frameworks surrounding data privacy, such as GDPR or CCPA, is crucial for organizations to navigate these complexities and avoid potential penalties.
Data privacy safeguards protect individuals from harm stemming from misuse of their personal information. These safeguards include robust security measures, transparent data policies, and clear consent mechanisms. Organizations must demonstrate a commitment to maintaining data privacy throughout the entire lifecycle of the data, from collection to deletion.
Security Measures for Data Protection
Implementing robust security measures is paramount to safeguarding sensitive data. This includes employing strong encryption protocols to protect data both in transit and at rest, using multi-factor authentication to verify user identities, and regularly updating software and systems to patch vulnerabilities.
Regular security audits and penetration testing are essential for identifying potential weaknesses in data protection systems. Proactive measures are crucial in mitigating risks and preventing data breaches. Furthermore, employee training on data security best practices is vital to ensure that all personnel understand their role in maintaining data confidentiality.
Consequences of Data Breaches
Data breaches can have severe repercussions, including financial losses, reputational damage, and legal liabilities. The costs associated with a data breach extend beyond the immediate financial impact; they often include significant expenses related to remediation, legal fees, and reputational recovery.
Breaches can erode public trust in organizations, leading to a loss of customer loyalty and future business opportunities. It is crucial for organizations to establish robust incident response plans that outline procedures for detecting, containing, and recovering from security breaches.
Ethical Considerations in Data Handling
Data handling extends beyond technical security measures; ethical considerations are paramount. Organizations must be transparent about their data practices, obtaining explicit consent from individuals before collecting and using their information. This includes clear communication about how data is used and for what purposes.
Ensuring data minimization is an ethical imperative, collecting only the necessary information for specific purposes. Furthermore, organizations should have clear policies regarding data retention, deletion, and access rights, allowing individuals to exercise control over their information.
Compliance and Legal Frameworks
Adherence to data privacy regulations, such as GDPR, CCPA, and others, is crucial for organizations operating globally. Understanding and complying with these regulations is essential to avoid legal penalties and maintain public trust. Navigating the complexities of different data privacy laws across jurisdictions can be challenging, requiring organizations to adapt their practices accordingly.
Understanding the specific requirements of each jurisdiction is vital for effective compliance. Organizations must ensure their data protection practices align with the legal requirements of all regions where they collect and process personal data. This involves ongoing monitoring and adaptation to evolving regulations.
Addressing the Liability and Responsibility in AV Hacking Incidents
Understanding the Scope of AV Hacking Liability
Analyzing AV (antivirus) hacking incidents requires a nuanced understanding of liability, encompassing not only the technical aspects but also the legal and ethical dimensions. This includes determining who is responsible for the damage caused by the breach, whether it's the developers of the AV software, the users of the software, or external actors exploiting vulnerabilities. The scope of liability extends to the direct and indirect consequences of the hack, such as financial losses, reputational damage, and potential legal repercussions. Identifying the specific actors and their roles in the incident is crucial to establishing appropriate accountability and preventing future occurrences.
Furthermore, the liability considerations extend to the chain of events leading to the incident. Was there a lack of adequate security measures implemented by the AV developers? Did the user fail to update the software, potentially creating a vulnerability? Or was it a sophisticated external attack exploiting a zero-day vulnerability? Determining the contributing factors is essential for developing effective mitigation strategies and assigning blame where appropriate.
Assessing the Responsibility of AV Software Developers
AV software developers bear a significant responsibility for the security and functionality of their products. Their obligation extends to proactively identifying and patching vulnerabilities, ensuring robust update mechanisms, and implementing comprehensive security testing procedures. A failure to meet these responsibilities can expose users to potential harm and lead to legal repercussions. Thorough documentation of security protocols, vulnerability reports, and incident response plans are critical aspects of this responsibility.
Moreover, the developers' responsibility extends to the transparency and communication surrounding security issues. Promptly addressing vulnerabilities and informing users about potential risks is crucial for mitigating the impact of potential attacks. The lack of such transparency can exacerbate the damage caused by a hacking incident and negatively affect the developer's reputation.
Evaluating User Responsibility in AV Hacking Incidents
While AV software developers bear a significant burden of responsibility, user actions also play a crucial role in the security posture. Failing to update the software regularly can leave systems vulnerable to known exploits, significantly increasing the risk of a successful attack. Users have a responsibility to maintain their software's integrity and follow security best practices. This includes implementing strong passwords, being cautious about suspicious emails or websites, and immediately reporting any unusual activity.
The level of user responsibility should be considered in context, recognizing that not all users have the same level of technical expertise. Education and awareness campaigns can help bridge the gap and empower users with the knowledge needed to protect themselves effectively. Providing clear guidelines and user-friendly tools can make a significant difference in minimizing user-related vulnerabilities.
Addressing the Role of External Actors in AV Hacking
External actors, such as hackers and malicious third parties, often play a significant role in AV hacking incidents. These individuals or groups may exploit vulnerabilities in the AV software, or other software on the system, to gain unauthorized access or cause damage. Investigating the motivations and tactics of external actors is crucial for developing effective countermeasures. This includes identifying patterns of behavior, analyzing attack vectors, and understanding the tools and techniques used in the attack.
Effective incident response protocols and proactive security measures are essential to deter external actors and minimize the impact of their attacks. Collaboration between AV developers, security researchers, and law enforcement is critical for effectively addressing these threats and preventing future incidents. Furthermore, understanding the evolving landscape of cyber threats is essential for staying ahead of malicious actors and adapting security strategies accordingly.