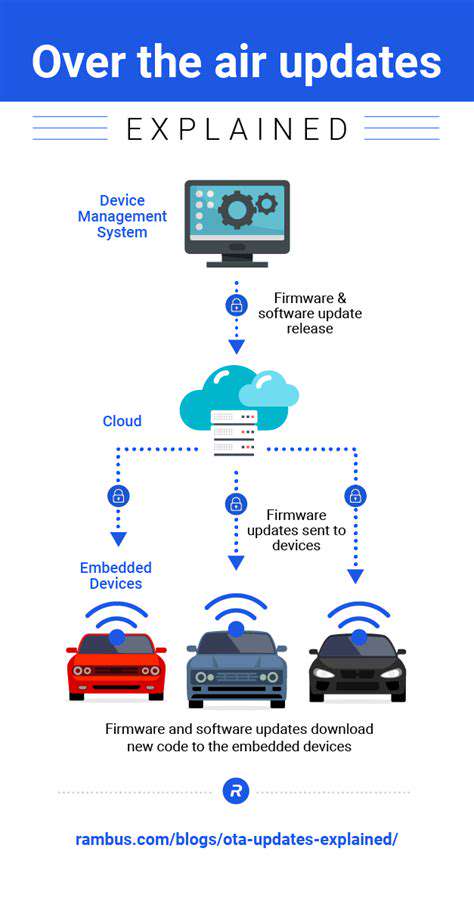
When programs don't work as intended, we encounter software glitches - those pesky errors that disrupt normal operations. These flaws manifest in countless ways, from frozen screens to complete system failures. What begins as a minor inconvenience can escalate into a serious security threat if left unaddressed. The process of tracking down these digital gremlins forms the backbone of quality software development.
Modern development teams employ sophisticated debugging techniques, combining automated tools with human expertise to hunt down programming errors. This relentless pursuit of perfection has led to innovative testing methodologies that catch issues before they reach end users. The result? Applications that behave predictably and withstand the demands of real-world use.
Exploitable Vulnerabilities: A Threat to Security
Cybercriminals constantly search for weaknesses in software like digital burglars checking for unlocked windows. These security holes, when discovered, become gateways for data theft and system manipulation. The most dangerous vulnerabilities often stem from oversights during the coding process - forgotten security checks or flawed logic that attackers can manipulate to their advantage.
White-hat security experts play a crucial role in this digital arms race, reverse-engineering software to uncover potential attack vectors before criminals do. Their findings help shape modern security standards and inform best practices that make systems more resistant to compromise.
Types of Software Glitches
Programming errors come in various flavors. Some cause calculators to give wrong answers, while others make web forms accept impossible dates. Memory leaks slowly choke systems, while race conditions create unpredictable behavior in multi-threaded applications. These digital imperfections often hide in plain sight, only revealing themselves under specific, sometimes rare, conditions that challenge the programmer's assumptions.
Causes of Glitches
Why do these errors occur? Sometimes it's rushing to meet deadlines, other times it's miscommunication between team members. Complex systems with many moving parts create countless opportunities for unexpected interactions. Even experienced developers occasionally transpose numbers or misinterpret requirements, proving that human fallibility remains a constant factor in software reliability.
The Impact of Glitches
A single misplaced decimal point once caused a spacecraft to miss Mars. While most bugs don't make headlines, their cumulative effect costs businesses billions annually. Beyond financial losses, software failures erode user trust and can endanger lives in critical systems like medical devices. When software controls airplanes or nuclear reactors, the margin for error shrinks to zero, making exhaustive testing protocols absolutely essential.
Exploitation Techniques
Hackers have developed an arsenal of methods to weaponize software flaws. They might flood a system with more data than it can handle or sneak malicious code through seemingly harmless input fields. Some attacks target the very memory spaces where programs store temporary information. Staying ahead of these threats requires developers to think like attackers, anticipating how each line of code might be twisted to malicious ends.
Preventing Glitches and Exploits
Building resilient software demands multiple layers of defense. Developers must validate every piece of incoming data, as if expecting an attack. Code reviews catch mistakes that automated tools miss, while simulated hacking attempts reveal real-world weaknesses. The most secure systems adopt a never trust, always verify approach, rigorously checking every operation and preparing for scenarios that should never happen.